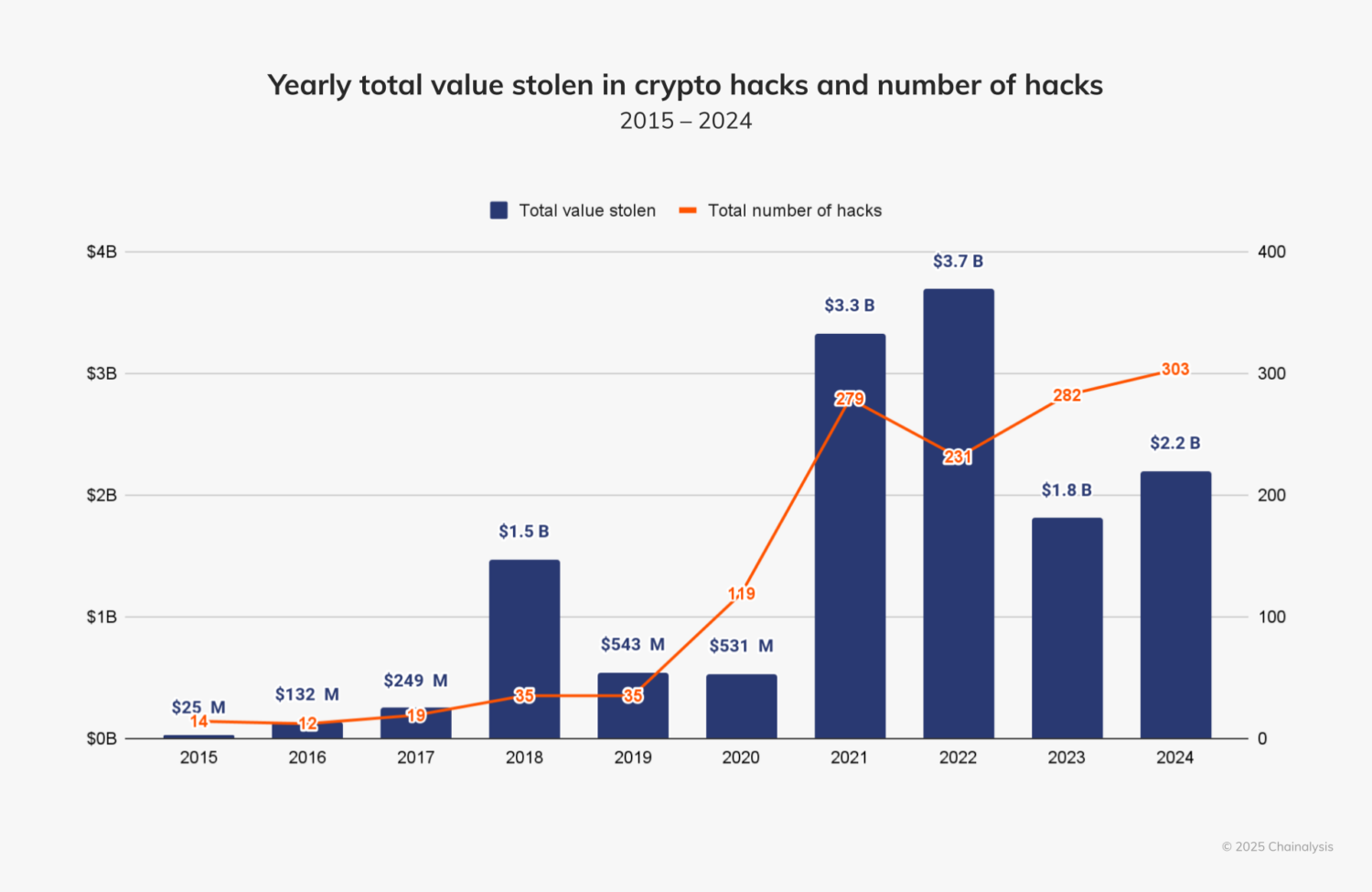
Clipboard hijacking malware poses a serious threat to cryptocurrency users—especially when attackers silently swap wallet addresses to steal funds. In 2024 alone, a staggering $2.2 billion was stolen worldwide due to crypto-related hacks and scams—a 21% increase over the previous year, according to chainalysis.com. Among these threats, clipboard hijackers are particularly insidious: they wait until you copy a crypto address, substitute it with one they control, and you unknowingly send your funds into the attacker’s pocket.
In this article, we’ll explore how clipboard hijacking malware tricks users into sending crypto to the wrong address, step through real-world case studies, and share actionable tips to detect and prevent losses. The goal is straightforward: help you understand the scam, recognize the warning signs, and protect your crypto safely.
What is Clipboard Hijacking Malware?
Clipboard hijacking malware is a type of malicious software designed to secretly monitor and manipulate the clipboard on your computer or mobile device. The clipboard is the temporary storage area your device uses when you copy and paste text—including sensitive data like cryptocurrency wallet addresses.
Unlike traditional viruses that destroy files or cause visible damage, clipboard hijacking malware operates quietly in the background. Its main purpose is to detect when a user copies a cryptocurrency address and then instantly replace it with the attacker’s own wallet address. This means when you paste the address into a transaction, you’re actually sending your crypto to the scammer, not your intended recipient.
Because crypto wallet addresses are long strings of random characters, most users only check the first and last few digits. Some attackers even use wallet addresses that share these same characters, making the swap even harder to spot—especially for high-value or targeted attacks. In most mass attacks, however, any attacker-controlled address will be substituted, relying on user inattention to complete the theft.
This method has become increasingly common as more people use cryptocurrencies, and the growing value of digital assets makes them a lucrative target for cybercriminals.
How Clipboard Hijacking Malware Steals Crypto
How Hackers Spread Clipboard Hijacking Malware
Clipboard hijacking malware typically reaches victims through several deceptive methods:
Phishing Websites: Attackers build fake crypto exchanges, wallet sites, or even fake CAPTCHA pages that prompt users to copy and paste suspicious commands. Once these commands are run, malware installs quietly in the background.
Malicious Downloads: Free software, browser extensions, unofficial crypto wallet apps, and cracked applications can be bundled with clipboard hijackers. After installation, the malware operates with little or no visible sign.
Phishing Emails and Messaging Apps: Cybercriminals send emails or messages with attachments or links that download the malware if clicked. Sometimes, these messages claim to be urgent updates or support from crypto services.
Compromised Websites and Ads: Even visiting a hacked or malicious site can sometimes exploit browser vulnerabilities, allowing the malware to be installed silently.
How the Malware Swaps Wallet Addresses
Once clipboard hijacking malware is installed, it constantly scans your clipboard for text strings that match the pattern of cryptocurrency wallet addresses (like those for Bitcoin or Ethereum). Here’s how the attack typically unfolds:
User Action: You copy a wallet address—perhaps to send funds to a friend or to deposit crypto on an exchange.
Automatic Replacement: The malware instantly replaces the copied address in your clipboard with one controlled by the attacker. This can happen so quickly that the user doesn’t notice.
Unwitting Transfer: When you paste the address into the transaction field, it’s the attacker’s address, not your intended recipient’s. You approve and send the crypto.
Funds Lost: Because blockchain transactions are irreversible, the crypto is sent directly to the attacker, and recovery is usually impossible.
Attackers often target large numbers of users, swapping any detected crypto address with their own. In more targeted cases, they may use “vanity” wallet addresses that share similar starting or ending characters with legitimate addresses, increasing the chance the user won’t spot the difference.
Example:
A crypto user copies their friend’s wallet address to send 0.1 BTC. The clipboard hijacker instantly replaces it with an attacker’s address. The user pastes and sends the funds, only realizing the theft when the friend reports not receiving the crypto.
Case Analysis: Real-World Crypto Theft Incidents
Clipboard hijacking malware has led to confirmed crypto losses in real-world campaigns. Below are two documented cases highlighting how attackers operated—and what went wrong.
Case A: GitVenom Campaign — $485,000 in Bitcoin Stolen via GitHub Trap
In late 2024, Kaspersky researchers uncovered GitVenom, a campaign distributing malware through fake GitHub repositories promoting tools for gamers and crypto users. These repositories secretly delivered a clipboard hijacker that replaced copied crypto wallet addresses with attacker-controlled ones. Victims worldwide—including in Brazil, Turkey, and Russia—lost roughly 5 BTC (≈ $485,000 at the time). The malware extracted wallet data and replaced addresses on the clipboard without detection.
Case B: Fake CAPTCHA Campaign Deploys Lumma Stealer / SecTopRAT
In early 2025, researchers documented fake CAPTCHA attacks where users visiting compromised websites were instructed to copy and paste commands into their Run dialog. This action installed malware—commonly Lumma Stealer or SecTopRAT—that included clipboard hijacking functionality. Once installed, the malware monitored and replaced cryptocurrency addresses in the clipboard. These attacks were broad and opportunistic, turning normal copy-paste actions into crypto theft vectors.
Key Lessons from Both Cases
| Lesson | Insight |
|---|---|
| Hidden Delivery, Real Theft | Both campaigns hid clipboard hijackers inside trusted-looking tools or sites—normal copy actions triggered the malware. |
| Irreversible Damage | Funds sent to attacker-controlled addresses were unrecoverable due to blockchain’s immutable nature. |
| Scale vs. Targeting | GitVenom used generic wallet addresses for mass infections; fake CAPTCHA attacks could serve both mass and high-value targets, sometimes using vanity-like addresses. |
How to Detect a Clipboard Hijacking Attack
Clipboard hijacking malware is designed to be stealthy, but there are warning signs that can help you spot an attack before it leads to crypto loss. Here’s what to look out for:
Warning Signs and Symptoms
Mismatch After Pasting: The most common clue is that the wallet address you paste does not match the one you copied. Always check at least the first and last five or six characters of the address before sending crypto.
Unexpected Address Changes: If you notice that an address in a text document, email, or crypto wallet has changed after pasting—or seems different each time you paste—it could be a sign your clipboard is being manipulated.
Pop-ups or Prompts to Copy Commands: Be cautious if a website prompts you to copy and paste strange commands or code into your system terminal, browser, or wallet app. This is a common way attackers get malware onto your device.
Strange Device Behavior: Other malware-related symptoms may include sudden computer slowdowns, unexpected error messages, or new programs/extensions you didn’t install.
Crypto Sent But Not Received: If you send crypto and the intended recipient reports not receiving it—even though the transaction is confirmed on the blockchain—immediately review your transaction details for any address mismatches.
Practical Detection Tips
Use Clipboard Monitoring Tools: Some security programs and specialized clipboard managers can track clipboard history and alert you to changes that occur between copying and pasting.
Manual Double-Checking: Make it a habit to compare the entire wallet address after pasting, especially for large transactions. Never rely solely on memory or partial address matching.
By staying alert to these warning signs and adopting double-checking routines, you greatly reduce your risk of falling victim to clipboard hijacking malware.
How to Prevent Crypto Address Swaps by Clipboard Hijackers
Staying one step ahead of clipboard hijacking malware is possible if you follow these proactive security measures:
1. Always Verify Wallet Addresses Before Sending
Double-Check the Address: Before you send any crypto, compare the full wallet address you pasted with the original one you intended to use. Even for small transactions, this simple step can save you from costly mistakes.
Check Multiple Characters: Don’t just glance at the first and last few characters—compare the entire address if possible.
2. Limit Copy-Paste Habits
Use QR Codes: When available, scan QR codes instead of copying and pasting addresses manually. QR codes are much harder for malware to intercept or modify.
Avoid Copy-Pasting From Unknown Sources: Never copy wallet addresses, commands, or scripts from unfamiliar websites, pop-ups, or messages.
3. Keep Your Devices Secure and Updated
Install Security Updates: Regularly update your operating system, browsers, and wallet apps to patch vulnerabilities that malware could exploit.
Use Reputable Security Software: Reliable antivirus and anti-malware solutions can detect and block many clipboard hijackers before they cause harm.
4. Use Secure Wallets and Extensions
Choose Wallets With Anti-Clipping Features: Some modern crypto wallets now include security features that alert you if an address is modified in your clipboard.
Beware of Browser Extensions: Only install browser extensions from official sources, and regularly review which extensions have access to your clipboard.
5. Practice Safe Online Behavior
Avoid Suspicious Downloads: Only download crypto tools, wallets, and software from official websites or verified app stores.
Be Wary of CAPTCHAs and Unusual Prompts: If a website asks you to copy and paste code or commands to “prove you are human,” it’s a red flag for malware.
6. Use Hardware Wallets for Large Transactions
Offline Protection: Hardware wallets keep your private keys and transaction signing offline, making clipboard hijacking nearly impossible for attackers to exploit.
By combining these habits and tools, you can dramatically reduce your risk of falling victim to clipboard hijacking malware—and keep your crypto safe from silent theft.
Best Practices for Crypto Transactions
Preventing clipboard hijacking malware is not just about technical defenses—it’s also about practicing good habits every time you move crypto. Here are the most important routines every user should adopt:
Manual Verification, Every Time
Copy-Verify-Paste-Send: Always follow this order: copy the wallet address, verify it after pasting, then send your funds. Take an extra moment to compare the address in your clipboard with the one displayed by the recipient or official platform.
Compare More Than Just a Few Characters: If possible, visually check the entire address string, not just the first and last segments.
Store and Use Trusted Addresses
Whitelist Frequent Addresses: Many exchanges and wallets let you “whitelist” or save known-good wallet addresses. Use this feature for regular contacts to avoid manual entry mistakes.
Never Reuse Pasted Addresses Blindly: Don’t trust addresses just because you’ve used them before—malware may have swapped them without your knowledge.
Educate and Inform Others
Share Knowledge: Teach friends, colleagues, and family members in crypto about clipboard hijacking risks. A simple tip could prevent major losses.
Report Suspicious Activity: If you notice malware behavior or lose funds to a clipboard hijacker, report it to your wallet provider or platform and consider notifying cybersecurity communities.
Use Multiple Devices for Large Transfers
Out-of-Band Verification: For significant transfers, confirm addresses using a separate device (such as a phone or hardware wallet) before hitting send.
Avoid Unnecessary Clipboard Use
Type Short Addresses: For internal transfers or exchanges, manually type short addresses when possible to eliminate clipboard risk.
By making these habits part of your routine, you minimize the risk of being tricked by clipboard hijacking malware—even if your device security is ever compromised.
Advanced Tips: Anatomy, Detection, and Manual Removal of Clipboard Hijacking Malware
Clipboard hijacking malware is designed to blend in and avoid detection. For technically-minded users or anyone concerned about a possible infection, understanding its structure and behaviors can help with identification and removal.
How Clipboard Hijacking Malware Works Internally
Process Monitoring: Most clipboard hijackers run silently as a background process or service. They constantly scan for clipboard events—specifically looking for data patterns that resemble cryptocurrency wallet addresses.
Address Database: Many variants carry a built-in list of attacker-controlled wallet addresses for multiple blockchains.
Persistence: To survive restarts, some hijackers add themselves to Windows startup or use scheduled tasks to relaunch automatically.
Common Forms: Clipboard hijackers can appear as Windows executables (.exe), malicious browser extensions, PowerShell scripts, or disguised as legitimate-looking system files.
Where Is Clipboard Hijacking Malware Stored?
Windows 11
Startup Folders: Malicious files may be placed in
C:\Users\[YourName]\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Scheduled Tasks: Open Task Scheduler (
taskschd.msc) and check for any unknown or suspicious tasks set to run on startup.Registry Run Keys: Some malware inserts itself into the registry:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
Temporary and Roaming Folders: Check for strange files in:
C:\Users\[YourName]\AppData\Roaming\C:\Users\[YourName]\AppData\Local\Temp\
Processes in Task Manager: Malware often disguises itself with generic names (like “svchost.exe” or “runtimebroker.exe”). Unusual memory usage or unfamiliar publisher names are red flags.
In macOS (Ventura, Sonoma, and later)
Launch Agents and Daemons:
~/Library/LaunchAgents//Library/LaunchAgents//Library/LaunchDaemons/
Malicious clipboard hijackers often create.plistfiles here to run on startup.
Application Support and Hidden Folders:
~/Library/Application Support/Unusual app folders or files without a clear source can be suspect.
Login Items:
Check System Settings > General > Login Items for unknown or suspicious apps/scripts.
Active Processes:
Use Activity Monitor to spot unknown processes using significant resources or with no publisher.
Malicious Apps or Scripts:
Sometimes appear as disguised apps or run via Automator, AppleScript, or unsigned binaries.
In Ubuntu Linux (and other modern Linux distros)
Autostart Entries:
~/.config/autostart/— Desktop malware may drop.desktopfiles to start scripts/apps at login.
User Crontabs:
crontab -e— Look for unfamiliar jobs scheduled to run at reboot or intervals.
Systemd Services:
~/.config/systemd/user/or/etc/systemd/system/— Custom services running suspicious scripts.
Hidden Scripts in Home Directory:
Malware may hide bash/python scripts in home directories, often named innocuously (e.g.,
.clipboard.py,.update.sh).
Unusual Running Processes:
Use
ps auxorhtopto review running user processes. Look for scripts or binaries with strange names or paths.
How to Manually Find and Remove Clipboard Hijacking Malware in Windows
Step 1: Identify Suspicious Behavior
If wallet addresses are being swapped, you likely have an active clipboard hijacker.
Step 2: Examine Running Processes
Open Task Manager (Ctrl+Shift+Esc).
Look for processes you don’t recognize, especially those without publisher information or with unusual names.
Step 3: Check Startup Items and Scheduled Tasks
In Task Manager, go to the “Startup” tab and disable anything suspicious.
Open Task Scheduler and look for recently created or odd-looking scheduled tasks.
Step 4: Inspect Key Folders
Browse the startup, Roaming, and Temp directories for new or recently modified files with odd names or no digital signature.
Right-click suspicious files and check their properties—legitimate system files should have a Microsoft or known publisher.
Step 5: Review Registry Run Keys
Open the Registry Editor (regedit.exe).
Carefully examine the aforementioned Run keys for any unfamiliar entries.
Warning: Editing the registry can harm your system—back up before making changes.
Step 6: Remove Malware
Delete suspicious files you’ve identified.
Remove any unknown scheduled tasks, startup entries, or registry keys related to the malware.
Restart your computer and confirm the behavior has stopped.
Step 7: Scan With Security Tools
Even after manual cleanup, run a full system scan with trusted anti-malware tools to catch any remnants.
Visual Example (For Reference)
Many clipboard hijackers use names like
systemupdate.exe,clipboard.exe, or random characters (e.g.,xyswq12.exe). If you see such files in odd locations or tied to startup, investigate further.
How to Manually Find and Remove on macOS
Check Login Items and Running Processes:
Remove any suspicious login items.
Force quit or inspect unknown processes in Activity Monitor.
Review Launch Agents/Daemons:
Look for recently added
.plistfiles or folders in the above directories.Delete those not tied to known apps.
Scan Application Support:
Remove odd or recently modified files/folders.
Delete and Empty Trash:
After removal, empty the Trash to prevent accidental restoration.
Run an Anti-Malware Scan:
Use a reputable Mac antivirus tool to confirm your system is clean.
How to Manually Find and Remove on Linux
Check Autostart and Cron:
Remove any
.desktopor script files in~/.config/autostart/not tied to apps you recognize.Clean out strange cron jobs (
crontab -e).
Inspect Systemd Services:
List user services:
systemctl --user list-units --type=serviceDisable and delete any suspicious services.
Review Running Processes:
Identify and kill any unfamiliar background scripts or binaries.
Check their full file path and delete if malicious.
Clean Home Directory:
Show hidden files (
ls -la ~) and delete anything odd (especially scripts starting with a dot).
Run Malware Scanners:
Tools like
rkhunter,chkrootkit, orClamAVcan help identify known threats.
Final Tips for All Systems
Always back up important data before deleting or modifying system files.
If you’re not sure about a process or file, search its name online or ask in a trusted tech forum.
After manual removal, keep your OS and all software updated, and change passwords for your crypto accounts just in case.
The Bottom Line
Clipboard hijacking malware is a stealthy but powerful threat, particularly for anyone dealing with cryptocurrencies. In recent years, attackers have refined their tactics—quietly swapping wallet addresses at the moment of transaction, spreading malware through phishing sites, malicious downloads, and even fake CAPTCHAs. Real-world cases have shown that even careful users can lose substantial amounts of crypto in a single, irreversible transaction.
The most important defenses are surprisingly simple:
Always double-check wallet addresses before sending funds.
Practice safe browsing and avoid suspicious downloads or prompts to copy commands.
Keep your operating system and security tools updated.
Be vigilant for unusual device behavior, and teach others to do the same.
For advanced users, understanding where clipboard hijacking malware hides—whether on Windows, macOS, or Linux—makes it possible to spot and remove threats manually when necessary. Good habits, technical awareness, and the right tools together provide the strongest protection.
In crypto, a single moment of inattention can lead to permanent loss. By staying alert, verifying every address, and regularly updating your security practices, you can protect your digital assets from even the most sophisticated clipboard hijacking malware.